Current Security Challenges for Businesses
Understanding the threats you defend against
The global events from the start of 2020 have brought unprecedented change to the physical and digital worlds. Cybercrime, however, is a constant. Cybercriminals continue—and sometimes escalate—their activity in times of crisis. Change brings opportunity, for both attackers and defenders. Defending against cybercriminals is a complex, ever-evolving, and never-ending challenge. For security professionals to create successful defence strategies, they need more diverse and timelier insights into the threats they are defending against.
The state of cybercrime
The threat environment we face continues to evolve. Cybercriminals are creative, well-resourced, well-organized, and innovative. They move quickly to discover new threat vectors, use new exploits, and respond to new defences. Attackers are opportunistic and will even switch lure themes daily in accordance with news cycles, as seen in cybercriminals’ use of the global COVID-19 pandemic to broadly target consumers, as well as to specifically target hospitals and healthcare providers.




- Credential phishing
- Business email compromise
- Combination of BEC & credential phishing
- Ransomware
- Malware
Credential phishing
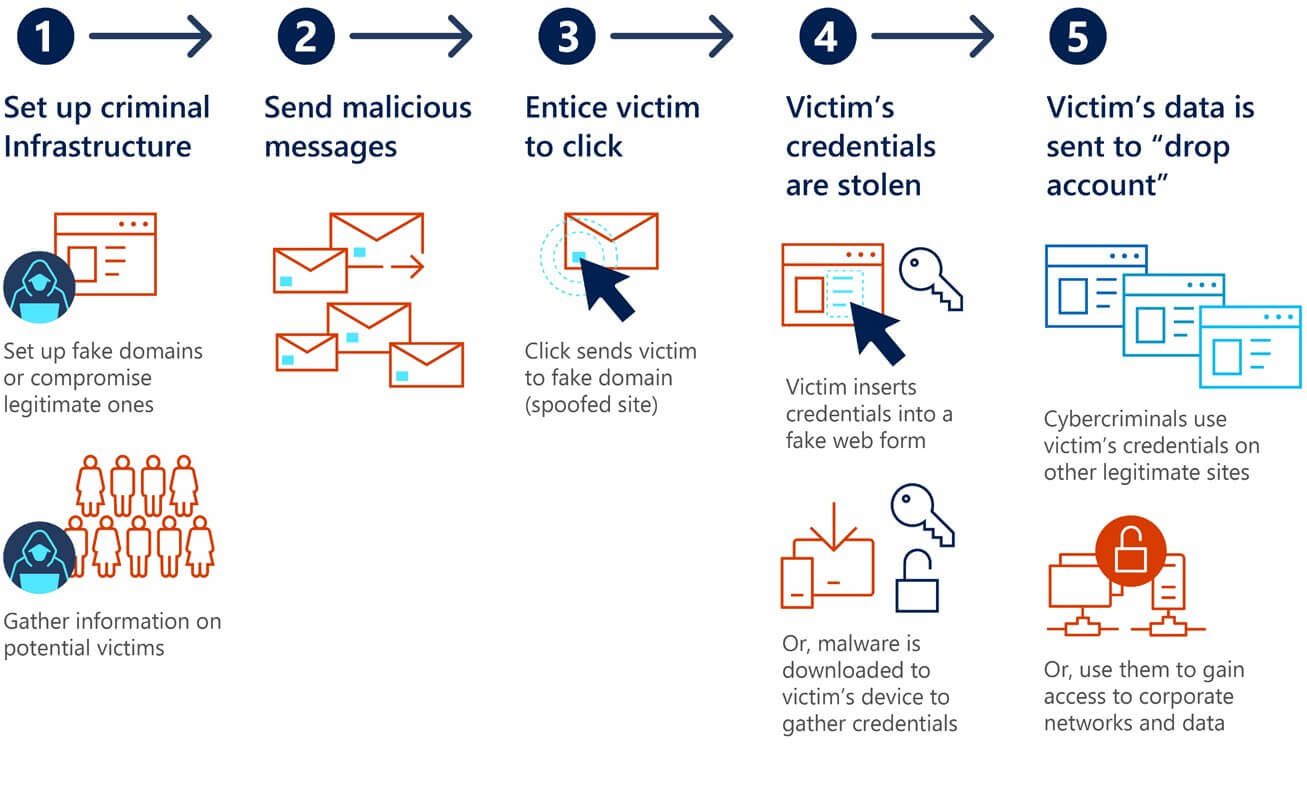
Business email compromise
Combination of BEC & credential phishing
Ransomware
Malware
Nation state threats
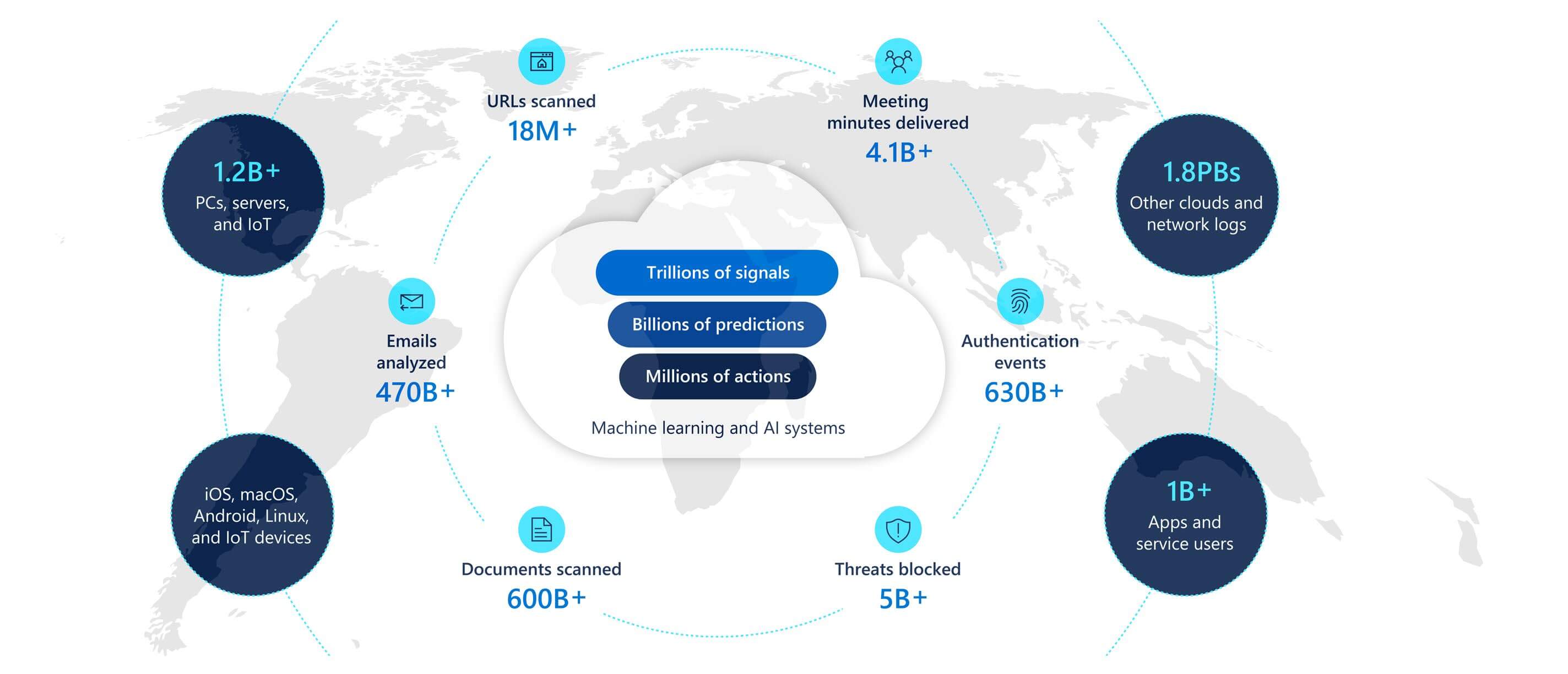
Microsoft tracks nation state activities to protect our platforms, our services, and our customers. We use a variety of metrics and sophisticated data integration techniques to better understand targeting, motivations, and customer impact. MSTIC focuses on nation state activities because these tactics, techniques, and procedures are often unique and novel, prompting downstream actors such as cybercriminals and smaller nation states to eventually copy their methods.
When a customer (organization or individual account holder) is targeted or compromised by nation state activities that Microsoft tracks, we deliver a nation state notification (NSN) to the customer. Over the past two years, Microsoft has delivered over 13,000 NSNs. The highest percentage of NSNs represented activity originating in Russia, followed by Iran, China, North Korea, and other countries.
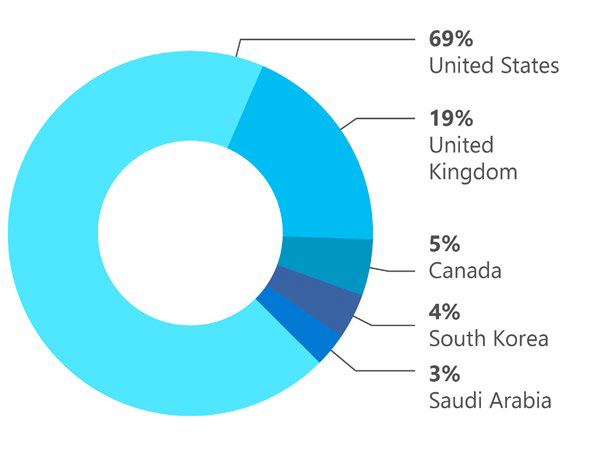
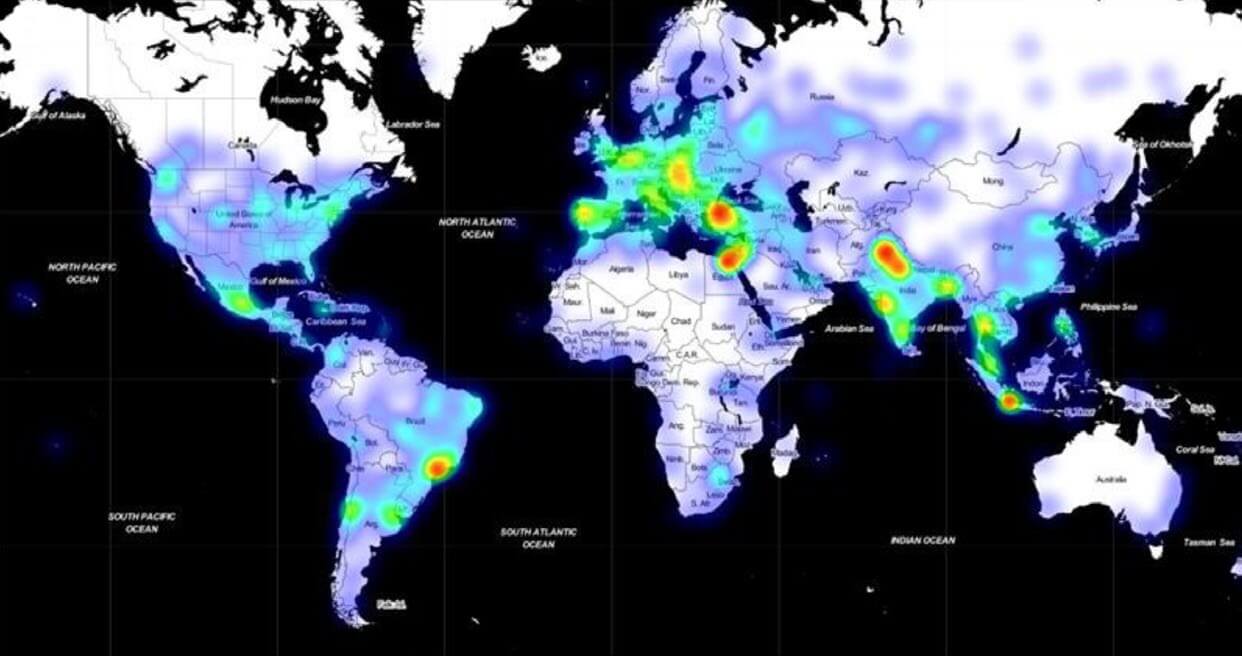
Top 5 targeted geographic regions based on NSNs (July 2019–June 2020)
Security and remote workforce concerns
Security decision makers in the United States perceive their most common remote workforce challenge as remote workers making choices that reduce security. Securing personal devices for remote work and the increase in phishing campaigns and identity fraud are also concerns.

Impact of the COVID-19 pandemic on Zero Trust deployment
By treating every access attempt as if it were originating from an untrusted network, the Zero Trust strategy helps solidify the security of VPNs for working from home. This is precisely the approach needed with today’s remote workforces because they’re coming from untrusted home networks and the VPN architectures used to extend corporate networks are sometimes failing

Organizations face a broad range of risks from insiders
Countless security officers across the world are now asking themselves, “Is my organization effectively prepared to identify and remediate increasing insider risks?” One reason for this question is COVID-19 and the subsequent rapid digital transformation it has forced organizations to undertake. According to a recent survey, the lives of up to 300 million information workers worldwide have been upended, and many are now working remotely with limited resources and increased stress.46 These employees are not only logging into enterprise environments and line-of-business applications but also accessing, editing, and sharing sensitive data.

Stressors that increase insider risks in a remote work environment